





B.Tech

M.Tech
Ph.D.

Add value to all stakeholders.Comprehensive skills, competence & experience has led to raise the height of academics.
 58 Lakhs
58 Lakhs 9.45 Lakhs
9.45 Lakhs
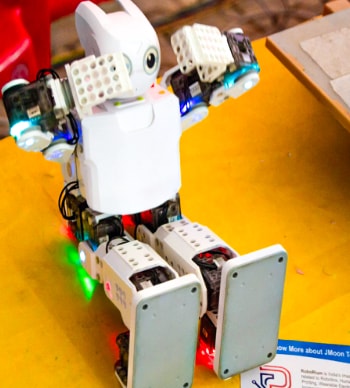
Here is what the best of student innovation looks like! Unleash your ambitions with our “Mega Projects”
 Athletics
Athletics
 Badminton
Badminton
 Basketball
Basketball
 Cricket
Cricket
 Football
Football
 Table Tennis
Table Tennis
 Tennis
Tennis
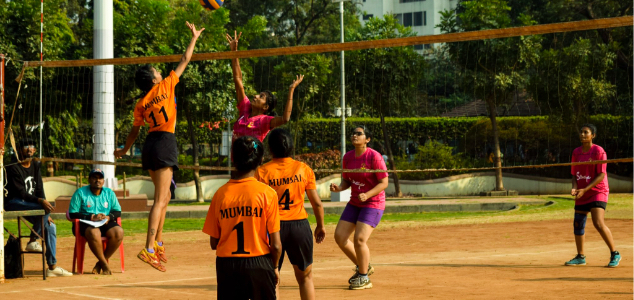 Volleyball
Volleyball
 Auditorium
Auditorium
 Canteen
Canteen
 Classroom
Classroom
 Computer Lab
Computer Lab
 AR-VR Lab
AR-VR Lab
 Laboratory
Laboratory
 Reading Area
Reading Area
 Seminar Hall
Seminar Hall